Microsoft's Azure Monitor Agent allows events to be directly written to certain Sentinel tables. In a previous blog piece 'Writing data to Sentinel's tables with REST and Data Collection Rules', I described how custom Data Collection Rules are written to allow Log Analytics / Sentinel tables to be written to using REST.
There doesn't seem to be a clear list of what tables do support direct writing. From trial and error, my understanding of those tables are listed below.
Sentinel Tables supporting direct writing
|
Anomalies |
ADAssessmentRecommendation |
|
ASimAuditEventLogs |
ADSecurityAssessmentRecommendation |
|
ASimAuthenticationEventLogs |
AzureAssessmentRecommendation |
|
ASimDhcpEventLogs |
DeviceTvmSecureConfigurationAssessmentKB |
|
ASimDnsActivityLogs |
DeviceTvmSoftwareVulnerabilitiesKB |
|
ASimFileEventLogs |
ExchangeAssessmentRecommendation |
|
ASimNetworkSessionLogs |
ExchangeOnlineAssessmentRecommendation |
|
ASimProcessEventLogs |
SCCMAssessmentRecommendation |
|
ASimRegistryEventLogs |
SCOMAssessmentRecommendation |
|
ASimUserManagementActivityLogs |
SfBAssessmentRecommendation |
|
ASimWebSessionLogs |
SfBOnlineAssessmentRecommendation |
|
AWSCloudTrail |
SharePointOnlineAssessmentRecommendation |
|
AWSCloudWatch |
SPAssessmentRecommendation |
|
AWSGuardDuty |
SQLAssessmentRecommendation |
|
AWSVPCFlow |
UCClientUpdateStatus |
|
CommonSecurityLog |
UCDOStatus |
|
GCPAuditLogs |
UCServiceUpdateStatus |
|
GoogleCloudSCC |
WindowsClientAssessmentRecommendation |
|
SecurityEvent |
WindowsServerAssessmentRecommendation |
|
Syslog |
|
|
WindowsEvent |
What is really interesting is the significance of large volume log sources and ASIM tables all being open for writing.
This provides the opportunity to use automation with external big data collectors (like Azure Data Explorer) in feeding events of significance to Sentinel.
UPDATE: December 2024
I have created a series of Bicep files that can be used in writing to these security related tables. These Data Collection Rules can be found at: https://github.com/LaurieRhodes/PUBLIC-Scripts/tree/main/Azure_Monitor_Agent/Data%20Collection%20Rules
After deploying a Data Collection Rule, you need to ensure that the Serice Principal you use for sending data to the DCR has the Monitoring Metrics Publisher role assigned to the rule.
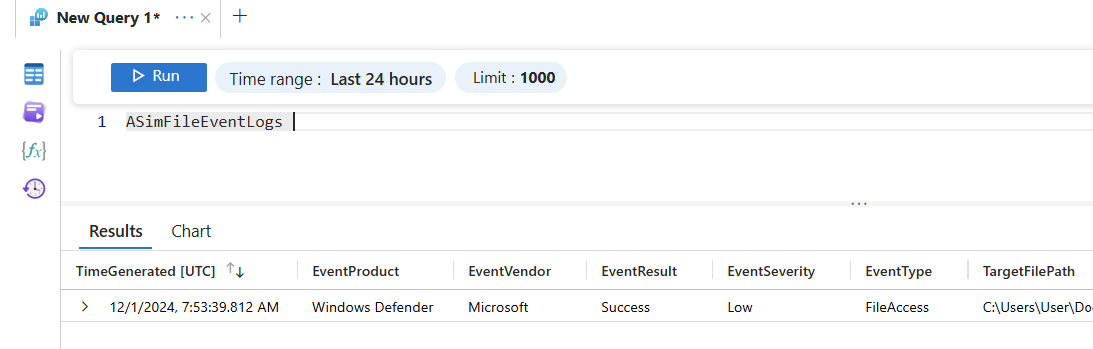
### Testing ASimFileEventLogs
$tenantId = "XXXXXXXXXXXXXXXXXXXXXXXXX" #Tenant ID the data collection endpoint resides in
$appId = "XXXXXXXXXXXXXXXXXXXXXXXXXX" #Application ID created and granted permissions
$appSecret = 'XXXXXXXXXXXXXXXXXXXXXXXXXX' #Secret created for the application
$dcrImmutableId = "dcr-XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX" #the immutableId property of the DCR object
$dceEndpoint = "https://XXXXXXXXXXXXXXXXXXXXXXXXX.ingest.monitor.azure.com"
$DCRStream = 'Custom-ASimFileEventLogs' # Must match your DCR
#Authenticate for a token
Add-Type -AssemblyName System.Web
$scope= [System.Web.HttpUtility]::UrlEncode("https://monitor.azure.com//.default")
$body = "client_id=$appId&scope=$scope&client_secret=$appSecret&grant_type=client_credentials";
$headers = @{"Content-Type"="application/x-www-form-urlencoded"};
$uri = "https://login.microsoftonline.com/$tenantId/oauth2/v2.0/token"
$bearerToken = (Invoke-RestMethod -Uri $uri -Method "Post" -Body $body -Headers $headers).access_token
# Invent some test data with ChatGPT!
$StartTime = Get-Date ([datetime]::UtcNow) -Format O
$EventData = @"
[ {
"TenantId": "00000000-0000-0000-0000-000000000000",
"SourceSystem": "OpsManager",
"TimeGenerated": "$($StartTime)",
"EventStartTime": "$($StartTime)",
"EventEndTime": "$($StartTime)",
"EventType": "FileAccess",
"SourceSystem": "Windows",
"EventMessage": "User accessed the file example.txt",
"RuleName": "File Access Rule",
"EventCount": 1,
"TargetFilePath": "C:\\Users\\User\\Documents\\example.txt",
"EventSubType": "Read",
"TargetFilePathType": "LocalDisk",
"EventResult": "Success",
"TargetFileName": "example.txt",
"EventResultDetails": "File accessed successfully",
"HashType": "MD5",
"EventOriginalUid": "evt-1234567890",
"SrcFileName": "example.txt",
"EventOriginalType": "FileAccess",
"SrcFilePath": "C:\\Users\\User\\Documents",
"SrcFilePathType": "LocalDisk",
"EventOriginalSubType": "Read",
"TargetFileCreationTime": "2024-10-01T09:00:00Z",
"EventOriginalResultDetails": "Success",
"TargetFileDirectory": "C:\\Users\\User\\Documents",
"EventSeverity": "Low",
"TargetFileExtension": "txt",
"EventOriginalSeverity": "Low",
"TargetFileMimeType": "text/plain",
"TargetFileMD5": "d41d8cd98f00b204e9800998ecf8427e",
"EventProduct": "Windows Defender",
"EventProductVersion": "1.2.3.4",
"TargetFileSHA1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"TargetFileSHA256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"EventVendor": "Microsoft",
"TargetFileSHA512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5711bb1fa635bb8a50c0cf1...",
"EventSchemaVersion": "2.0",
"TargetFileSize": 1024,
"EventOwner": "User",
"SrcFileCreationTime": "2024-10-01T09:00:00Z",
"EventReportUrl": "https://example.com/report",
"SrcFileDirectory": "C:\\Users\\User\\Documents",
"RuleNumber": 101,
"SrcFileExtension": "txt",
"ThreatId": "THREAT-12345",
"SrcFileMimeType": "text/plain",
"ThreatName": "FileAccessThreat",
"SrcFileMD5": "d41d8cd98f00b204e9800998ecf8427e",
"SrcFileSHA1": "da39a3ee5e6b4b0d3255bfef95601890afd80709",
"ThreatCategory": "FileAccess",
"SrcFileSHA256": "e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855",
"ThreatRiskLevel": 2,
"SrcFileSHA512": "cf83e1357eefb8bdf1542850d66d8007d620e4050b5711bb1fa635bb8a50c0cf1...",
"ThreatOriginalRiskLevel": "Medium",
"SrcFileSize": 1024,
"ThreatConfidence": 80,
"ActingProcessCommandLine": "C:\\Windows\\System32\\cmd.exe /c type example.txt",
"ThreatOriginalConfidence": "High",
"ActingProcessName": "cmd.exe",
"ThreatIsActive": "True",
"ActingProcessId": "1234",
"ThreatFirstReportedTime": "2024-10-01T10:00:00Z",
"ActingProcessGuid": "process-1234-5678",
"ThreatLastReportedTime": "2024-10-07T12:30:00Z",
"NetworkApplicationProtocol": "TCP",
"ThreatField": "File Access",
"ThreatFilePath": "C:\\Users\\User\\Documents\\example.txt",
"DvcIpAddr": "192.168.1.10",
"DvcHostname": "User-PC",
"DvcDomain": "WORKGROUP",
"DvcDomainType": "Local",
"DvcFQDN": "User-PC.local",
"DvcDescription": "User's Personal Computer",
"DvcId": "PC-12345",
"DvcIdType": "UUID",
"DvcMacAddr": "00:1A:2B:3C:4D:5E",
"DvcZone": "Internal",
"DvcOs": "Windows 10",
"DvcOsVersion": "10.0.19042",
"DvcAction": "File Read",
"DvcOriginalAction": "Read",
"DvcInterface": "Ethernet",
"DvcScopeId": "Scope-001",
"DvcScope": "Internal Network",
"ActorUserId": "user123",
"ActorUserAadId": "aad-user-12345",
"HttpUserAgent": "Mozilla/5.0",
"AdditionalFields": "{\"CustomField1\": \"Value1\", \"CustomField2\": \"Value2\"}",
"ActorUserSid": "S-1-5-21-1234567890-123456789-1234567890-1001",
"ActorUserIdType": "LocalUser",
"ActorScopeId": "Scope-001",
"ActorScope": "Internal",
"ActorUsername": "user123",
"ActorUsernameType": "Local",
"ActorUserType": "StandardUser",
"ActorOriginalUserType": "StandardUser",
"ActorSessionId": "Session-1234",
"TargetAppId": "App-001",
"TargetAppName": "Text Editor",
"TargetAppType": "Desktop",
"TargetOriginalAppType": "Desktop",
"TargetUrl": "file://C:/Users/User/Documents/example.txt",
"SrcIpAddr": "192.168.1.10",
"SrcPortNumber": 445,
"SrcHostname": "User-PC",
"SrcDomain": "WORKGROUP",
"SrcDomainType": "Local",
"SrcFQDN": "User-PC.local",
"SrcDescription": "User's Personal Computer",
"SrcDvcId": "PC-12345",
"SrcDvcIdType": "UUID",
"SrcDvcScopeId": "Scope-001",
"SrcDvcScope": "Internal Network",
"SrcDeviceType": "Laptop",
"SrcGeoCountry": "Australia",
"SrcGeoLatitude": "-33.8688",
"SrcGeoLongitude": "151.2093",
"SrcGeoRegion": "NSW",
"SrcGeoCity": "Sydney",
"SrcRiskLevel": 1,
"SrcOriginalRiskLevel": "Low",
"SrcMacAddr": "00:1A:2B:3C:4D:5E",
"EventSchema": "ASimFileEventLogs"
}
]
"@
# Send the data to Log Analytics
$headers = @{"Authorization"="Bearer $($bearerToken)";"Content-Type"="application/json"}
$uri = "$($dceEndpoint)/dataCollectionRules/$($dcrImmutableId)/streams/$($DCRStream)?api-version=2021-11-01-preview"
$uploadResponse = Invoke-RestMethod -Uri $uri -Method "Post" -Body $EventData -Headers $headersYou can verify the results in your Log Analytics Workspace...
- Log in to post comments