One of the benefits of Azure Data Explorer is it's UI portal for users. Staff members don't need Infrastructure permissions to An Azure subscription, the portal URL is enough to be able to do run queries against any data in a database.
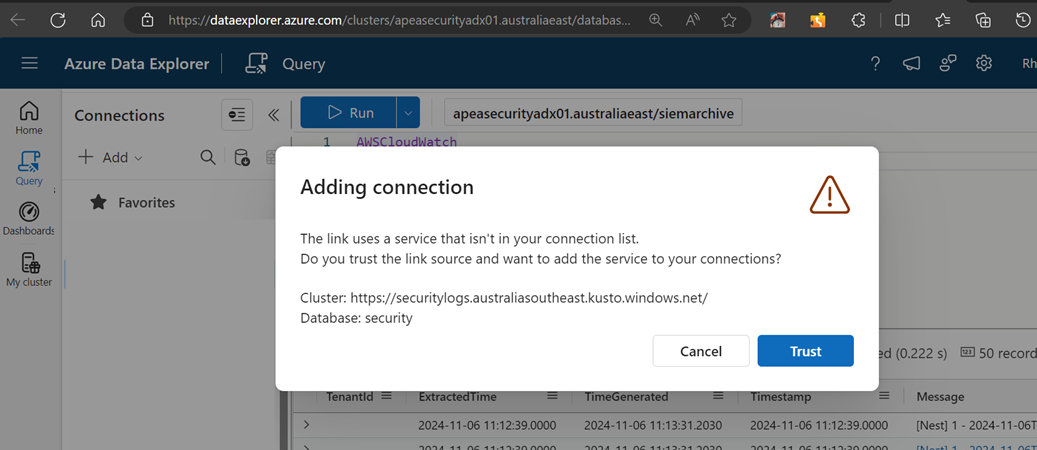
When opening Azure Data Explorer (Web UI) from a shared URI, staff members may be prompted with a dialog stating: "This link uses a service that isn't in your connection list. Do you trust the link source and want to add the service to your connections?"
There is a current 'feature' that can prevent authorised users from having access to the database. The error presented is "Principal 'aaduser=xxxxx is not authorized to perform operation 'VersionShowCommand' on <ADX Server>'"
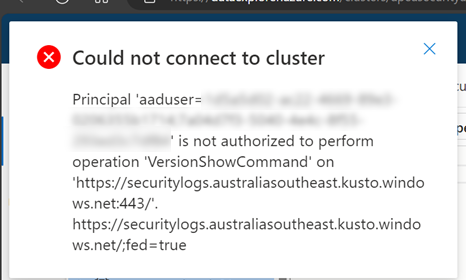
You can share access to the ADX database different types of users including external guests. What I learned painfully that this error isn't strickly a permissions issue, it's more likely to be highlighting that the way Azure Data Explorer if referencing a user doesnt align to an account that has had permissions assigned to the ADX database. In this case, the user account is an 'aaduser' account.
To resolve this, you need to modify permissions using KQL on the database that is being attempted to be accessed. You can see the existing permissions using the command:
.show database DatabaseName principals
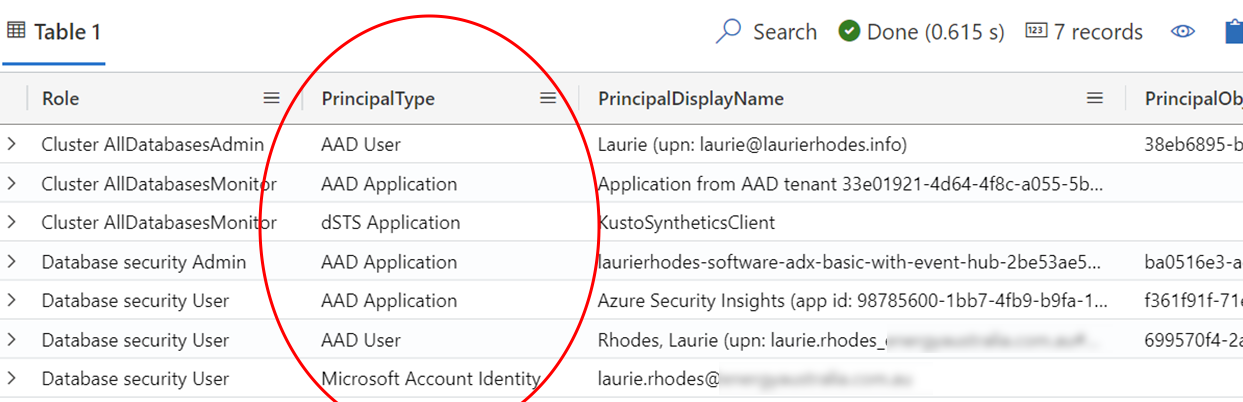
Currently, I've come across issues with external guest accounts, replicated accounts added to a database via groups and inconsistencies with some individual accounts that are added to the ADX database. Whatever the coding reasons causing these issues, the fix is to take note of the error displayed as it displays how the account is being interpreted by the ADX UI Portal.
We can then specifically add the account based on the format notation that will be used by ADX with that particular user.
.add database <database name> users ('msauser=xxxxxxxxxxxxxxxxxxxxx:xxxxxxxxxxxxxxxxxxxx)This Microsoft reference discusses in more detail how to try and refer to accounts when adding permissions via KQL.
https://learn.microsoft.com/en-us/kusto/management/reference-security-principals?view=microsoft-fabric
- Log in to post comments