This example is from provisioning a Windows client on Azure and using a bootstrap (Custom Script Extension) for using PowerShell DSC (Pull) off a Server 2016 (WMF 5) DSC server.
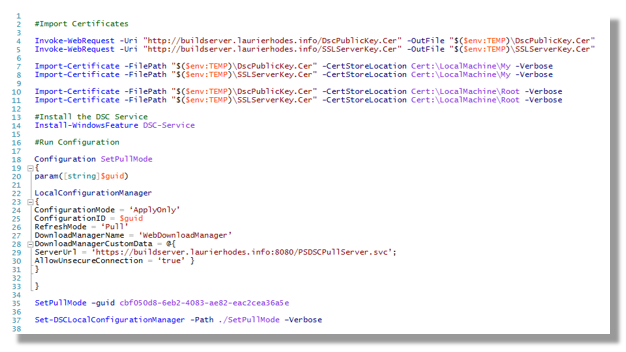
I’m using Self-Signed certificates in my environment. One certificate is for the webserver of my DSC server. The second certificate is for DSC to use for encryption.
I use the Custom Script Extension to ensure that both certificates are trusted by importing them into the machine certificate store.
After the certificates are imported, I ensure the PowerShell DSC Feature is installed.
I also configure the Local Configuration Manager to point to my DSC Pull Server.
Note that the GUID I have specified matches a generic DSC Pull Sequence that has been created on the DSC Pull Server
Windows Management Framework 5.1
The problem we currently face is using mixed versions of Windows Management Framework between the DSC Pull Server and clients. Azure Marketplace Images are not consistent with the version of the framework used and this leads to a decryption problem with received MOF files if you use Server 2016 against Windows Server 2012 R2 provisioned clients.
The solution is to upgrade Windows Management Framework as part of the bootstrap install.
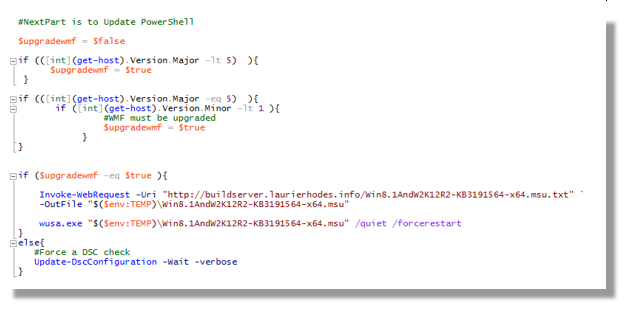
I’ve copied the Microsoft Update File for WMF to an accessible server (as my machines can’t download from the internet). As it’s the last part of my bootstrap, I forcibly reboot the machine as part of the upgrade.
Once the machine restarts it will be able to decrypt the MOF files being pulled from the DSC Pull Server
Complete Bootstrap
#Import Certificates
Invoke-WebRequest -Uri "http://buildserver.laurierhodes.info/DscPublicKey.Cer" -OutFile "$($env:TEMP)\DscPublicKey.Cer"
Invoke-WebRequest -Uri "http://buildserver.laurierhodes.info/SSLServerKey.Cer" -OutFile "$($env:TEMP)\SSLServerKey.Cer"
Import-Certificate -FilePath "$($env:TEMP)\DscPublicKey.Cer" -CertStoreLocation Cert:\LocalMachine\My -Verbose
Import-Certificate -FilePath "$($env:TEMP)\SSLServerKey.Cer" -CertStoreLocation Cert:\LocalMachine\My -Verbose
Import-Certificate -FilePath "$($env:TEMP)\DscPublicKey.Cer" -CertStoreLocation Cert:\LocalMachine\Root -Verbose
Import-Certificate -FilePath "$($env:TEMP)\SSLServerKey.Cer" -CertStoreLocation Cert:\LocalMachine\Root -Verbose
#Install the DSC Service
Install-WindowsFeature DSC-Service
#Run Configuration
Configuration SetPullMode
{
param([string]$guid)
LocalConfigurationManager
{
ConfigurationMode = ‘ApplyOnly’
ConfigurationID = $guid
RefreshMode = ‘Pull’
DownloadManagerName = ‘WebDownloadManager’
DownloadManagerCustomData = @{
ServerUrl = ‘https://buildserver.laurierhodes.info:8080/PSDSCPullServer.svc’;
AllowUnsecureConnection = ‘true’ }
}
}
SetPullMode –guid cbf050d8-6eb2-4083-ae82-eac2cea36a5e
Set-DSCLocalConfigurationManager -Path ./SetPullMode –Verbose
#NextPart is to Update PowerShell
$upgradewmf = $false
if (([int](get-host).Version.Major -lt 5) ){
$upgradewmf = $true
}
if (([int](get-host).Version.Major -eq 5) ){
if ([int](get-host).Version.Minor -lt 1 ){
#WMF must be upgraded
$upgradewmf = $true
}
}
if ($upgradewmf -eq $true ){
Invoke-WebRequest -Uri "http://buildserver.laurierhodes.info/Win8.1AndW2K12R2-KB3191564-x64.msu.txt" `
-OutFile "$($env:TEMP)\Win8.1AndW2K12R2-KB3191564-x64.msu"
wusa.exe "$($env:TEMP)\Win8.1AndW2K12R2-KB3191564-x64.msu" /quiet /forcerestart
}
else{
#Force a DSC check
Update-DscConfiguration -Wait -verbose
}- Log in to post comments